Posted in : Security By Rickard Carlsson Translate with Google ⟶
5 years ago
Phishing is an attack concept where an attacker usually contacts a victim pretending to be from a trustworthy source to get information that they shouldn’t have gotten if they used their real identity.
When an attacker targets specific individuals or groups within an organization the phishing method is called spear phishing. According to Symantec ISTR report volume 23 from 2018, the majority of organized security breaches used spear phishing as the infection vector.
One of the reasons why these attacks are so effective and commonly used is because the attack is built to exploit people’s feelings. It will also require less effort to write a mail and pretend to be from a supplier and trick a victim into clicking on a link or open an attachment instead of putting in the time and effort to find a way through a firewall or other security solution. Usually malware is being spread with these emails in form of malicious links or malicious attachment. When the user clicks on the link or opens the attachment the malicious code will be executed in the victim’s system.
This has been a common problem for years now and many users are aware that you shouldn’t open files from unknown sources but are you equally careful when clicking on links? If you find the description interesting, you will most likely just click on the link without actually reading the domain name before and that is another weakness an attacker can exploit.
Example on link-manipulation
Let’s say that you work for the company xyz and that your website is ‘xyz.com’. An attacker could then create a malicious website with a similar name, for example ‘secure-xyz.com’ or use a legit domain but with a redirect to a malicious site.
- http://www.secure-xyz.com
- http://www.xyz.com/amp/http://www.badsite.com
They could also encode the URL to make it harder to read or shorten it
- http://www.xyz.com%2Fexit.asp%3FURL%3Dhttp%3A%2F%2Fwww.badsite.com
- https://bit.ly/2TZB50k
Generally, you should keep attention to links that you think look weird and if you are not sure where the link leads to you shouldn’t visit it. It is better to be safe than sorry and today there are great tools available online where you can scan for malicious content and one of them is
To use it you just enter a URL and press enter. Multiple anti malware-engines will then scan the URL.
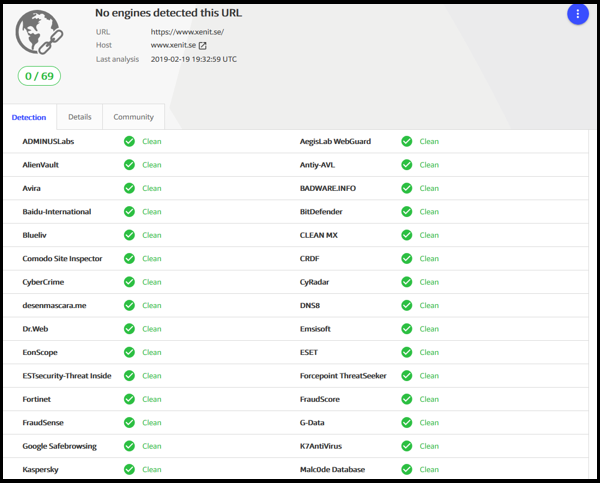
And for this test we can see that no engines detected our URL ‘https://www.xenit.se’ as malicious.
This and similar tools are great but the best way to reduce the risk of becoming a victim to this kind of attacks is to arrange awareness training for all employees regularly. Below you will find a link to a quiz where you will put your ability to identify phishing emails to test. You will inspect some emails and then you have to decide if you think it is malicious or not and afterwards you will get a good explanation on why or why not it is malicious.
Link to quiz:
https://phishingquiz.withgoogle.com/
Were you able to identify all phishing mails? Please leave a comment with your result or if you want to discuss phishing further.
Tags : awareness, infosec, malware, phishing, Security, spear, training
Personlig rådgivning
Vi erbjuder personlig rådgivning med författaren för 1400 SEK per timme. Anmäl ditt intresse i här så återkommer vi så snart vi kan.
Add comment