Posted in : Exchange, Office 365 Av Jonas Back Översätt med Google ⟶
5 years ago
Are you running Exchange Online and still allow Basic Authentication (a.k.a. Legacy Authentication) for all users and not running MFA? Then you’re extremely exposed to attacks. Microsoft has announced the blocking of this on 13 Oct 2020 but the biggest problem is that you probably will get (and possibly already have been) breached because of it.
The truth is that it’s more just to start blocking Legacy Authentication. Once you start blocking it, ActiveSync will stop working for many users. This would also bring the discussion how to configure and roll-out MFA. And once you’re there, there’s a discussion how to configure your mobile devices since many devices don’t support ActiveSync with MFA. This also brings the discussion whether to require Outlook Mobile since this offers more security features which also results in a discussion regarding MDM. So if you’re in for such a project, contact us and we can assist.
In this post I will not explain how to configure your Conditional Access policies to block Legacy Authentication it but rather how to discover which users are actually running Legacy Authentication so you can evaluate your current usage and why it’s important to fix it.
What’s the problem with Legacy Authentication? It requires only username and password and we cannot require a 2nd factor of authentication, for example a one-time password. These older protocols such as SMTP, POP, IMAP and MAPI simply does not have this feature and does not understand it.
But I have enabled MFA? Sure, but if you don’t explicitly block legacy authentication, users will still be able to login using legacy authentication leaving the accounts vulnerable to attacks. We have seen many times that customers have enabled MFA (only) and then a few weeks later, the user gets breached and looking at the logs you see the user got breached via SMTP/IMAP/POP. Therefore, Legacy Authentication has to be blocked explicitly.
But I still need SMTP/POP/IMAP? That is very common. In the best of all worlds, you can switch the application(s) requiring this to modern authentication protocols. That is your first choice. But for the very few instances you still require legacy authentication, set a very secure password and make an exception. That would result in just a few accounts that legacy authentication still enabled. But beware, techniques like leaked credential lists and password spraying attacks will probably get you breached anyway.
How can I find which users are still using Legacy Authentication? Simple, go to portal.azure.com > Azure Active Directory > Sign-ins and use a filter:
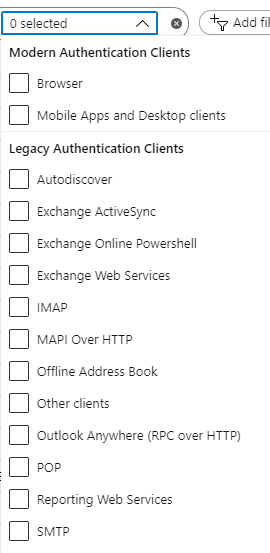
This will allow you to filter out what might require legacy authentication in the future. But remember, just because someone use legacy authentication today does not mean they require it in the future – there might be better ways to do it.
It might be hard sometimes to filter if the log is huge. One possibility is to Download and then use Excel to filter more in detail. Another option is to use portal.azure.com > Azure Active Directory > Workbooks and choose a report:
Tags : Azure AD, Exchange Online
Personlig rådgivning
Vi erbjuder personlig rådgivning med författaren för 1400 SEK per timme. Anmäl ditt intresse i här så återkommer vi så snart vi kan.


Add comment