Posted in : Microsoft, Windows Server Av Stina Perbo Utas Översätt med Google ⟶
8 years ago
Applocker is a great resource to avoid malicious code and applications, however it’s not always easy to inventory the applications in your environment.
To solve this Applocker can be configured to audit only for a time and clients can upload logs to a server which can then be filtered with powershell into a easy to filter report.
First a GPO must be configured with enforce or audit only rules.
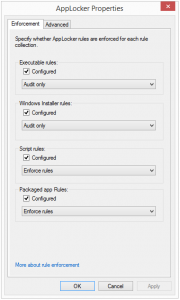
Then an Event subscription manager needs to be configured (details at the end of the post).
When a server is configured the subscriptions needs to be configured, set up a subscription per applocker policy type.
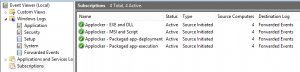
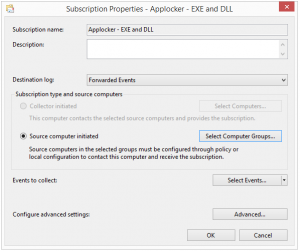
The logs should now be collected by the server and presented in the Forwarded Events log.
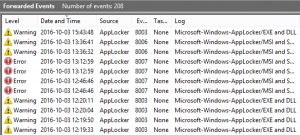
However the data is only available in XML view and sorting through hundreds of logs manually is often not a valid approach. This is where powershell comes to the rescue.
The script below can be run on the collector server or remotely and outputs valuable data to a gridview report. The gridview can in turn be copied to an excel sheet for further processing.
$Logs = Get-WinEvent -LogName 'ForwardedEvents' #-ComputerName $remoteServer
#Create datatable and add headers
$DataTable = new-object System.Data.dataTable
'Computer','TimeCreated','Level','LogType','FilePath','FileHash','Publisher','EventID','Message' | ForEach-Object{$DataTable.Columns.Add($_) | Out-Null}
$Logs | ForEach-Object{
$Applocker = $false
$thisLog = $_
$xmlLog = [xml]$thisLog.ToXml()
#Filter out non-applocker rules
if($xmlLog.Event.RenderingInfo.Provider -eq 'Microsoft-Windows-AppLocker'){$Applocker = $true}
If($Applocker){
$row = $DataTable.NewRow()
$row.Computer = $xmlLog.Event.System.Computer
$row.TimeCreated = $xmlLog.Event.System.TimeCreated.SystemTime
$row.Level = $xmlLog.Event.RenderingInfo.level
$row.LogType = $xmlLog.Event.RenderingInfo.Channel
$row.FilePath = $xmlLog.Event.UserData.RuleAndFileData.FilePath
$row.FileHash = $xmlLog.Event.UserData.RuleAndFileData.FileHash
$row.Publisher = $xmlLog.Event.UserData.RuleAndFileData.Fqbn
$row.EventID = $xmlLog.Event.System.EventID
$row.Message = $xmlLog.Event.RenderingInfo.Message
$DataTable.Rows.Add($row)
}
}
$DataTable | Out-GridView -Title "Forwarded Events"
Configure Source initiated subscription:
https://msdn.microsoft.com/en-us/library/bb870973(v=vs.85).aspx
Tags : Applocker, EventViewer, PowerShell
Personlig rådgivning
Vi erbjuder personlig rådgivning med författaren för 1400 SEK per timme. Anmäl ditt intresse i här så återkommer vi så snart vi kan.


Comments
L1ttl3j1m says
Thanks for a very useful script! Can I also add, you can convert timeCreated to your local time by going;
$row.timeCreated=(get-date($xmlLog.Event.System.TimeCreated.systemtime)).addhours()
is a plus or minus value, so .addhours(+10) for Sydney, or .addhours(-5) for New York
To output to 24 hour time in the CSV, you can add .tostring('HH:mm:ss dd/mm/yyyy') Other date/time formats are also permissible
Vikingur Saemundsson says
Hi, thanks for the comment, I hope it came to use and saved some time filtering through applocker audit events.
If you would like to go the extra mile and be RFC compliant with datetime object. Check the blogpost https://www.xenit.se/techblogg/datetime-and-rfc3339-compliance-in-powershell-a-deepdive/ for more information. In the post I assumes UTC but "local" can be chosen instead.
Add comment